Expense reimbursement fraud is one of the most common forms of asset misappropriation worldwide, and mischaracterized expenses sit at the centre of it. In this scheme, employees submit personal, non-business or inflated costs and classify them as legitimate business expenses. What makes it particularly damaging is that it often blends in with normal operations, small, frequent claims that accumulate into significant losses over time.
For UAE businesses, this risk is amplified by high-volume travel, distributed teams, vendor-heavy operations and reimbursement workflows that rely heavily on manual review. When receipts, approvals and coding are handled inconsistently, mischaracterized expenses bypass detection easily. The financial cost is only part of the problem; the bigger issue is compromised internal controls, inaccurate financial statements and erosion of trust across teams.
This is why finance leaders increasingly treat expense fraud not as an administrative irregularity, but as a governance issue. Understanding how mischaracterized schemes work, and where they hide, is the first step toward strengthening internal control.
Key Takeaways
- Mischaracterized expense schemes occur when employees classify personal costs as business expenses.
- They rely on ambiguity, inconsistent documentation, and gaps in manual review.
- Red flags appear in patterns, repeated merchants, threshold-level claims, weekend spending, vague descriptions.
- Effective controls include policy clarity, automated receipt validation, card restrictions and analytics.
- Technology significantly reduces the window in which expense fraud can occur.
What Is a Mischaracterized Expense Scheme?
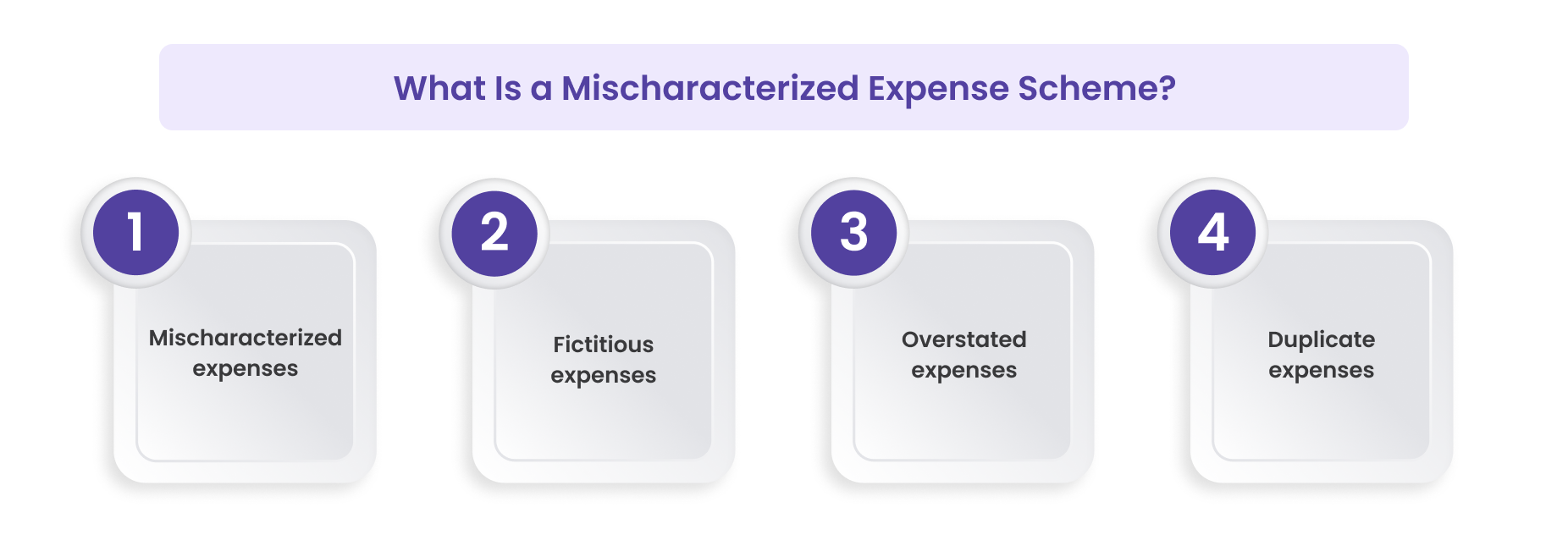
A mischaracterized expense scheme occurs when an employee claims personal expenses as business-related, disguising them within the company’s reimbursement framework. It is one of the four well-established categories of expense reimbursement fraud recognised in forensic accounting and internal audit literature. The four categories are:
- Mischaracterized expenses: personal costs claimed as business
- Fictitious expenses: fabricated receipts or purchases that never occurred
- Overstated expenses: inflating legitimate costs beyond the actual amount
- Duplicate expenses: submitting the same cost multiple times
Mischaracterized expenses are often the hardest to detect because they can appear plausible on the surface, a meal labelled as a client meeting, a hotel stay described as business travel, or fuel purchases coded as operational spending. Without strong internal controls or contextual data, these entries blend seamlessly into legitimate expenses.
Also read: A Comprehensive Guide to Travel and Expense Management Process
How Perpetrators Commit Mischaracterized Expense Fraud

Employees rarely submit obviously fraudulent claims. Instead, they exploit grey areas where policies are vague, documentation is weak or review processes rely on trust rather than verification.
Submitting personal purchases as business expenses
This is the most common form of mischaracterization. Employees may classify weekend restaurant bills, personal gifts, family travel or household purchases as work-related. Without detailed receipts or supporting context, these claims often slip through routine checks.
Reframing personal travel as business travel
Flights taken for holidays may be partially coded as business travel by adding a superficial meeting reference. Hotel stays can be misrepresented as part of a work trip, especially when travel and hospitality budgets are large and decentralized.
Using corporate cards for non-business spending
Some employees use company cards for personal purchases and later provide vague or misleading justifications. Finance teams that rely solely on card statements, without merchant validation, receipt scrutiny, or automated categorization, struggle to identify these transactions.
Altering or manipulating receipts
Fraudsters may modify dates, remove personal items from a bill, or use screenshots rather than actual receipts. Edited images and altered digital invoices are increasingly common, particularly when receipts are submitted through manual channels.
Passing expenses through other individuals
Employees may route personal expenses through friends or family, using third-party invoices to mask the payment trail. These cases are harder to detect without pattern analysis or exception monitoring.
Mischaracterized expense schemes thrive in environments where controls are fragmented. When approvals occur quickly, documentation standards vary across teams, and policies lack specificity, fraud becomes easier and more widespread.
Also read: 8 Steps for Effective Employee Expense Management in the UAE
Red Flags and Detection Signals Finance Teams Should Watch For

Mischaracterized expenses rarely appear as dramatic anomalies. They show up as patterns, subtle deviations in behaviour, inconsistencies across categories, or claims that only look unusual when viewed in context. Internal auditors and forensic accountants often identify these schemes by examining behavioural patterns rather than individual transactions.
Unusual spending patterns within the same role or team
If one employee consistently submits higher meal, travel, or fuel expenses than peers with similar duties, it is often a precursor to misclassification. Large outliers or steady “creep” in spend levels are early indicators that require deeper review.
Expenses consistently just below approval thresholds
Fraudsters learn internal workflows quickly. Claims that repeatedly fall just under limits that bypass additional approvals, such as AED 499 when AED 500 triggers manager review, are a classic signal of manipulation.
Receipts that lack detail or appear repetitive
Simplified or generic receipts, especially from merchants that rarely provide item-level detail, should prompt further checks. Repeated claims with the exact same amounts, time stamps, or vendor locations indicate possible fabricated or reused documentation.
Mismatch between transaction date and business activity
If expenses occur on weekends, public holidays, or during periods when the employee had no work-related travel scheduled, mischaracterization is likely. Cross-referencing expense timing with operational schedules can expose such inconsistencies.
High use of “miscellaneous” or ambiguous categories
Fraudsters often exploit vague COA categories that lack clear guidelines. Entries coded as “general”, “other”, or “miscellaneous” deserve closer scrutiny, especially when repeated frequently.
Employees who resist documentation requirements
Consistent delays in submitting receipts, reluctance to provide explanations, or pushback on policy controls suggest a higher probability of mischaracterization.
These signals don’t prove fraud, but they warrant closer investigation. Strong controls rely on early pattern detection rather than catching isolated incidents after the fact.
Also read: Improving Internal Control over Financial Reporting (ICFR)
Real-World Examples of Mischaracterized Expense Schemes
To understand how these schemes materialise, it helps to look at real patterns seen across internal audits. The following examples are anonymised but reflect recurring fraud behaviours documented across the industry, including in public audit findings and global case studies.
A sales manager claiming personal dining as client meetings
A senior employee repeatedly submitted meal expenses from upscale restaurants, citing “client entertainment.” Over time, auditors noticed the absence of client names, inconsistent meeting records and identical guest counts. Cross-checking CRM activity revealed no meetings on those dates. The pattern exposed over AED 70,000 in personal dining coded as business expenses.
Weekend hotel stays framed as project-related travel
An employee extended personal trips by attaching a one-day “project visit” to justify weekend accommodation. Receipts showed check-in dates misaligned with approved travel schedules. HR records confirmed no client activity during that period. The mischaracterized costs accumulated across multiple departments before detection.
Fuel purchases unrelated to approved routes
In a logistics-heavy business, repeated fuel purchases appeared at stations far outside the employee’s assigned delivery routes. Telematics data later confirmed the vehicle had not visited those locations. The employee had been refuelling a personal car using the company card.
Third-party invoices used to conceal personal expenses
A staff member funnelled personal spending through a family-owned vendor, submitting invoices labelled as “operational materials.” Without a vendor-verification process, these claims were approved for months. When procurement flagged inconsistencies, auditors uncovered a circular invoicing arrangement designed to mischaracterize expenses.
Patterns like these highlight why reactive controls are insufficient. Fraud often hides behind routine documentation unless companies combine policy clarity with data-driven monitoring.
Why Manual Review Fails at Scale
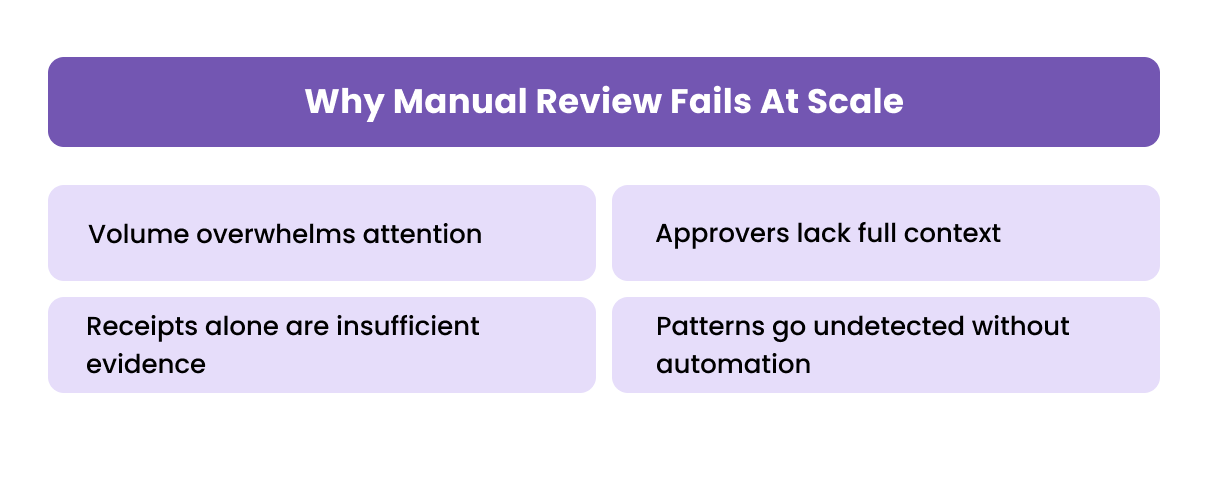
Most mischaracterized expense schemes succeed not because they are sophisticated, but because finance teams rely on processes that simply cannot scale. Manual review creates blind spots that fraudsters exploit.
Volume overwhelms attention
High-growth businesses and multi-location teams generate hundreds or thousands of expense entries each month. Reviewers rarely have the time to cross-check every line item with operational schedules, policies or prior claims.
Approvers lack full context
Managers approving expenses often see only a receipt and a short description. They may not know whether similar claims were submitted recently, whether spending patterns are consistent with peers, or whether the vendor is legitimate.
Receipts alone are insufficient evidence
A receipt shows only that money was spent, not why or whether the expense benefited the business. Fraudsters often rely on this misconception when mischaracterizing personal purchases.
Patterns go undetected without automation
Mischaracterization becomes obvious only when analysing trends, repeated merchants, recurring amounts, location mismatches, or timing anomalies. These patterns rarely emerge through manual checks.
Manual review has a role, but cannot shoulder the entire burden. The combination of policy, system controls, and automated validation is what significantly reduces mischaracterized schemes.
Also read: Steps to Automate Expense Management and Approvals
Controls That Actually Work: Prevention and Detection
Mischaracterized expense schemes thrive in environments where policies are vague, documentation standards vary across teams, and reviews depend on individual judgement rather than system-enforced rules. Effective controls are layered: policy, process, technology, and oversight. When these layers reinforce each other, fraud becomes far harder to execute or conceal.
Clear, enforceable policies
A policy that simply states “submit valid business expenses” is insufficient. Policies must specify:
- What qualifies as a legitimate business expense
- What documentation is required for each category
- What is expressly prohibited
- When manager approval is required
- How exceptions should be handled
The more precise the definitions, the less room there is for interpretation.
Consistent documentation verification
Documentation must be evaluated for both validity (receipt authenticity, TRN, invoice details) and context (whether the expense aligns with business purpose). For travel and entertainment, additional details, such as agenda, client names, or activity logs, strengthen the audit trail.
Automated detection of duplicate and unusual claims
Duplicate claims are one of the easiest forms of fraud to commit and the hardest to detect manually. Automation identifies:
- repeated amounts
- reused receipts
- identical time stamps
- merchant repetition beyond expected patterns
Automated comparisons across employees, timeframes, and departments surface anomalies that manual reviewers miss.
Merchant category and transaction-level controls
Corporate card controls add a strong preventative layer. Restricting merchant categories, blocking cash withdrawals, limiting weekend use, and preventing transactions outside approved regions reduces opportunities for mischaracterization before they occur.
Periodic analytics and forensic reviews
Quarterly or semi-annual audits reveal patterns masked by month-to-month variability. Useful analyses include:
- spend per employee vs role benchmarks
- vendor or merchant concentration
- weekend or off-hours transactions
- high incidence of “miscellaneous” categories
- employees with unusually low receipt submission compliance
These reviews inform policy adjustments and training.
The most robust environments combine these layers so no single point of failure enables fraud.
Role-based approval workflows
Approval logic should reflect the risk level of the expense. High-value or high-risk categories, such as travel, gifts or fuel, should route through finance or compliance reviewers rather than only line managers. Rotating approvers helps prevent collusion.
[cta-3]
Response Playbook When Fraud Is Suspected
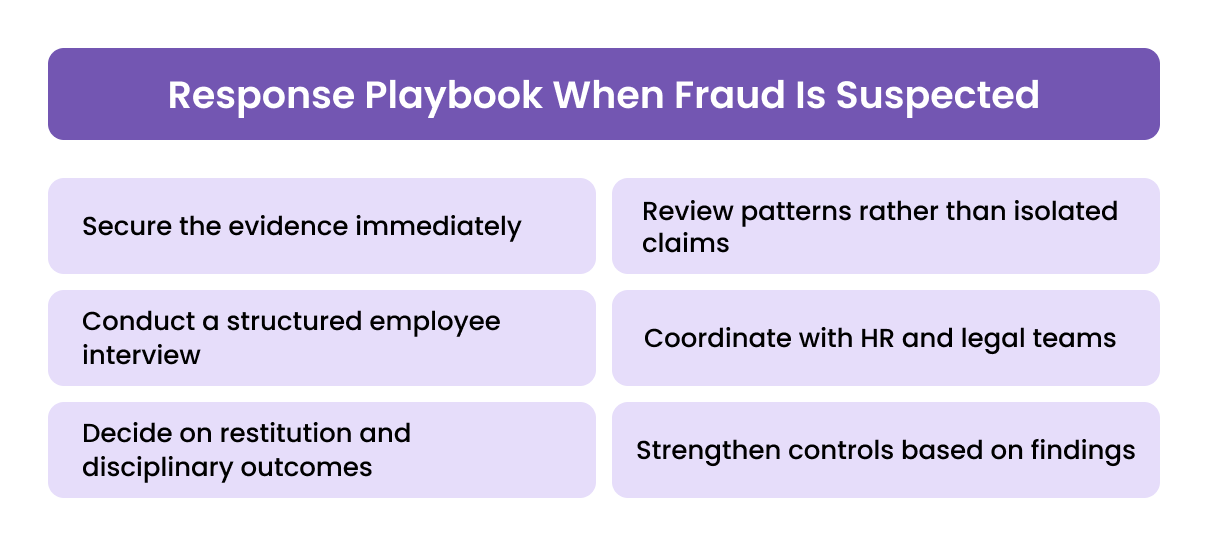
Once a mischaracterized expense scheme is identified, or even suspected, the response must be structured and evidence-driven. Mishandling these situations risks losing documentation, escalating employee conflict or compromising legal requirements.
1. Secure the evidence immediately
Freeze the relevant transactions in the system, restrict editing access, and collect the associated receipts, approval logs, comments and digital trails. If corporate cards are involved, temporarily suspend the card to prevent further misuse.
2. Review patterns rather than isolated claims
A single questionable claim may be an error, but repeated patterns across months indicate intent. Analyse:
- frequency
- categories
- timing
- merchant behaviour
- comparison with peer group
Pattern analysis provides clearer grounds for escalation.
3. Conduct a structured employee interview
Approach the discussion factually, focusing on discrepancies between receipts, stated purpose and supporting logs. Avoid speculation or accusatory language; employees often reveal context that clarifies misunderstandings or exposes deliberate mischaracterization.
4. Coordinate with HR and legal teams
Fraud investigations may involve employment actions, restitution, terminations or legal reporting obligations. Ensuring documentation is handled in compliance with UAE labour law and internal disciplinary frameworks is essential.
5. Decide on restitution and disciplinary outcomes
If fraud is confirmed, actions may include repayment, formal warning, demotion or termination. Decisions should be consistent across employees and aligned with documented policy to avoid claims of unfair treatment.
6. Strengthen controls based on findings
Each incident reveals control weaknesses. Whether it's unclear policy wording, overly broad approval privileges, or gaps in documentation rules, investigations should lead to measurable improvements.
A disciplined response protects the organisation, reinforces accountability and strengthens its governance framework.
Also read: 10 Expense management practices to optimise finances
How Alaan Reduces Mischaracterized Expense Schemes
Mischaracterized expenses rely on ambiguity, manual gaps and slow detection. Alaan addresses these failure points by embedding controls directly into the spending process, where risk originates, rather than relying solely on after-the-fact reviews.
Real-time visibility into every card transaction
When employees use Alaan corporate cards, the spend appears instantly in the dashboard. Finance teams see the merchant, amount, category and location without waiting for month-end reconciliation. This immediacy helps detect early signs of mischaracterization, such as atypical merchant behaviour or irregular transaction timing.
Automated receipt capture and AI verification
Alaan Intelligence extracts TRN, invoice details and VAT fields from uploaded receipts, comparing them against the transaction. Missing receipts, mismatches or altered documents are flagged for review. This prevents fabricated or manipulated receipts from passing through unnoticed.
Policy enforcement at the transaction level
Instead of relying on employees to follow policy, Alaan enforces it. Finance teams can configure rules that:
- block prohibited merchant categories
- restrict spending to approved suppliers
- set department-level limits
- prevent off-hours or off-location transactions
These settings stop mischaracterized expenses before they enter the system.
Duplicate and anomaly detection
Alaan recognises repeated receipts, duplicate values, unusual spend spikes, and exceptions relative to peer benchmarks. This allows finance teams to identify questionable behaviour in minutes rather than during quarterly audits.
Seamless ERP integration for clean audit trails
Each transaction syncs to the ERP with correct coding, tax treatment, and documentation. This reduces misclassification, ensures consistency across reporting periods, and simplifies external audits.
[cta-9]
Alaan doesn’t replace internal controls; it amplifies them by eliminating manual workload and narrowing the gap where fraud typically slips through.
Conclusion
Mischaracterized expense schemes rarely appear as dramatic wrongdoing. They take shape quietly, one ambiguous meal claim, one personal taxi ride coded as business, one weekend hotel stay justified with a vague description. Over time, these small distortions compromise financial accuracy, weaken governance, and create patterns of behaviour that are far harder to reverse.
For finance teams, the priority is not only detecting fraud after it occurs, but preventing it through clear definitions, consistent documentation, structured approvals, and system-level controls. When organisations rely solely on manual review, mischaracterized expenses gain too much room to hide. When policies, processes, and automation work together, fraud becomes significantly harder to execute and easier to identify early.
A disciplined approach protects more than the bottom line; it reinforces trust across the organisation and ensures financial reporting reflects reality, not interpretation.
At Alaan, we help companies eliminate mischaracterized expenses by combining real-time card controls, automated receipt verification, duplicate detection, and seamless ERP syncing.
If you want stronger protection against reimbursement fraud and a cleaner, more reliable audit trail, book a demo to see how Alaan transforms spend governance end to end.
Frequently Asked Questions (FAQs)
1. What is an example of a mischaracterized expense?
A common example is an employee claiming a personal meal, weekend hotel stay or family travel as a business expense by providing a vague description or fabricated justification.
2. How does mischaracterized expense fraud differ from fictitious or duplicate expenses?
Mischaracterized expenses involve real purchases incorrectly coded as business-related. Fictitious expenses involve fabricated receipts, while duplicate expenses involve submitting the same claim more than once.
3. What are the most common signs of expense report fraud?
Frequent claims just below approval thresholds, repeated vendors, weekend spending, missing receipts, and expenses inconsistent with business schedules are typical indicators.
4. Can mischaracterized expenses be prosecuted as fraud?
Yes. If intent is proven, it can constitute financial misconduct under internal policies and, in serious cases, legal action. Outcomes depend on the extent of fraud, the documentation used, and the jurisdiction.
5. Why do companies struggle to detect mischaracterized expenses?
Manual reviews are time-limited and context-limited. Approvers often lack visibility into patterns across time, departments, or employee groups. Fraud hides in these gaps.
6. How does Alaan help prevent mischaracterized expense schemes?
Alaan enforces spending rules at the transaction level, verifies receipts automatically, detects anomalies, blocks prohibited merchant categories, and syncs accurate data into the ERP, reducing both intentional and accidental misclassification.


.avif)






